As an authentication method, passwords obviously suck. But we’re stuck with them and have to make the most of them.
The reason passwords suck is because data breaches have rendered them nearly useless. Over 5 billion records were breached last year and many of those records contained your passwords and sign-on credentials to sites you regularly use.
Most People Use Bad Passwords
2 years ago (in 2018), KeeperSecurity performed an analysis of compromised hacked data and made some startling conclusions. Americans use really dumb passwords with alarming regularity.
In fact, 17% of accounts are protected with the stupidest password of all ‘123456″. It’s hard to believe that 1 in 5 accounts in the US are protected with something so simple.
The analysis conducted on information from 10 million breached accounts showed that the following passwords were most commonly found in the dataset.
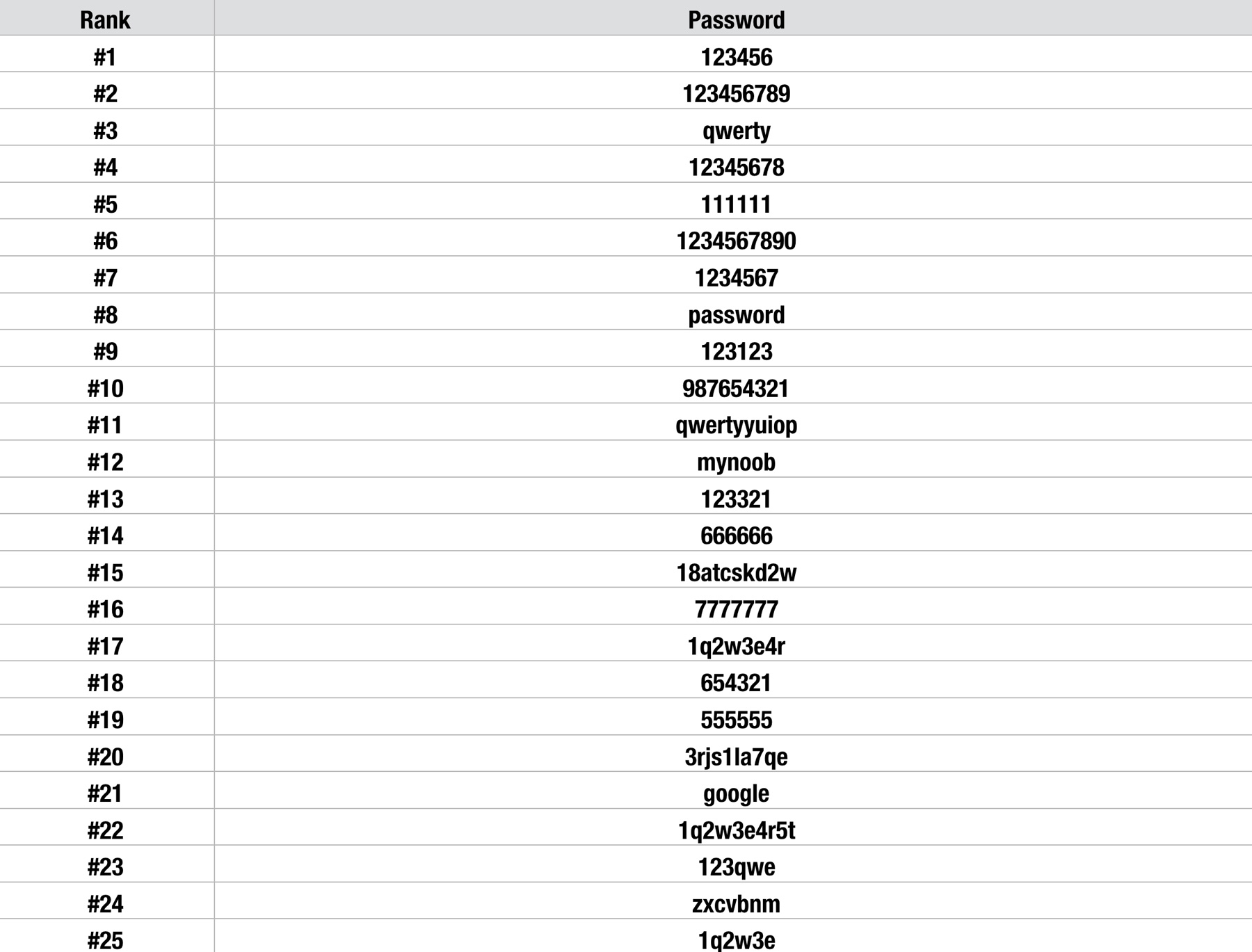
As you can tell, people tend to use bad passwords that follow predictable patterns. These predictable patterns can be exploited by hackers.
KeeperSecurity made the following conclusions about these dumb passwords:
- The list of most-frequently used passwords has changed little over the past few years.. That means that user education has limits. While it’s important for users to be aware of risks, a sizable minority are never going to take the time or effort to protect themselves. IT administrators and website operators must do the job for them.
- Four of the top 10 passwords on the list – and seven of the top 15 – are six characters or shorter. This is stunning in light of the fact that, as we’ve reported, today’s brute-force cracking software and hardware can unscramble those passwords in seconds. Website operators that permit such flimsy protection are either reckless or lazy.
- The presence of passwords like “1q2w3e4r” and “123qwe” indicates that some users attempt to use unpredictable patterns to secure passwords, but their efforts are weak at best. Dictionary-based password crackers know to look for sequential key variations. At best, it sets them back only a few seconds.
- Email providers don’t appear to be working all that hard to prevent the use of their services for spam. Security expert Graham Cluley believes that the presence of seemingly random passwords such as “18atcskd2w” and “3rjs1la7qe” on the list indicates that bots use these codes over and over when they set up dummy accounts on public email services for spam and phishing attacks. Email providers could do everyone a favor by flagging this kind of repetition and reporting the guilty parties.
How Long Will It Take To Hack Your Password?
CyberSecurity experts have analyzed password patterns and have created a matrix that can tell how long hackers would need to crack your password and the results are enlightening. There is a reason that websites require combinations of numbers and letters, upper and lowercase, and special characters.
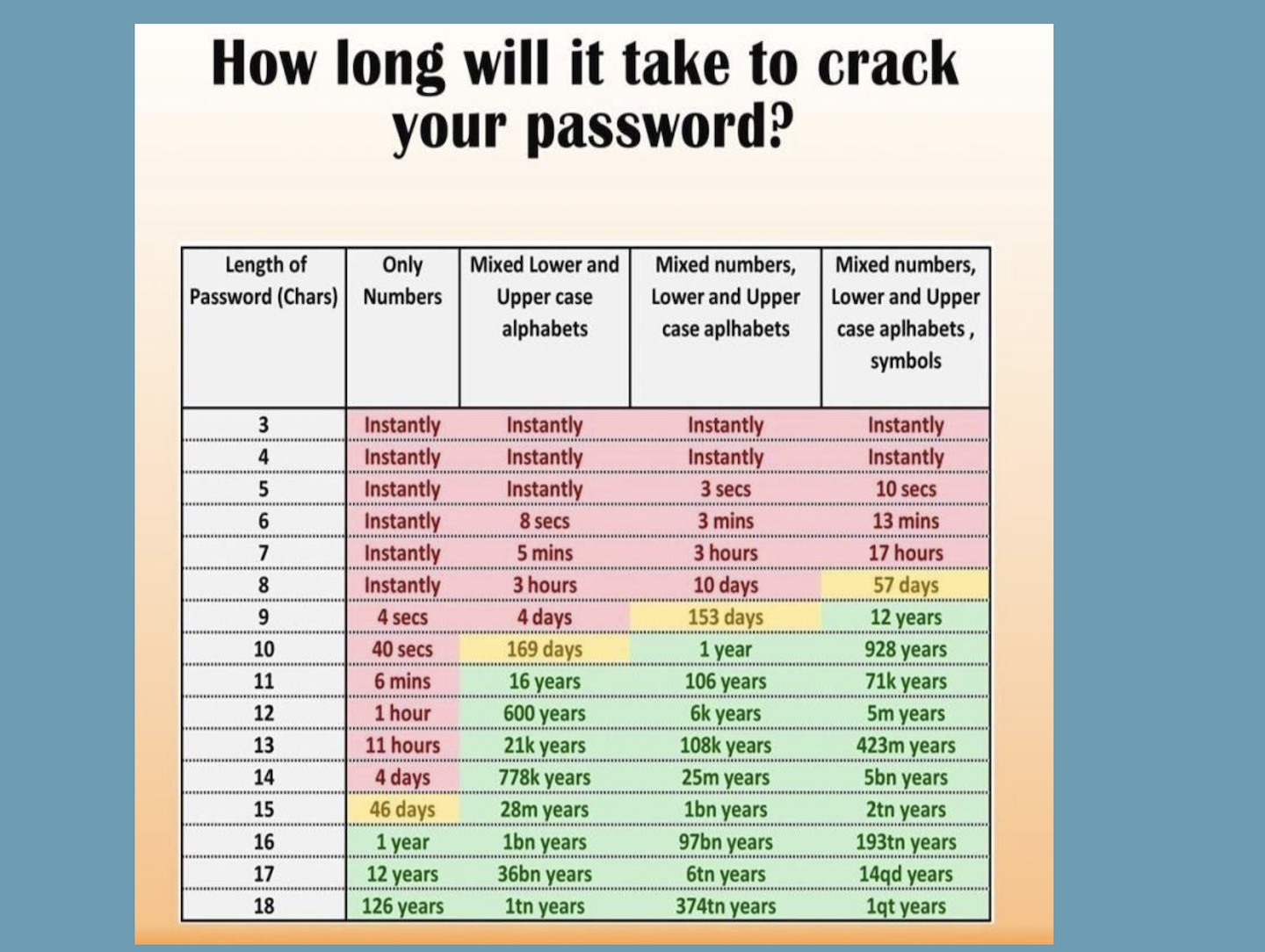
Original post by Frank McKenna, Chief Fraud Strategist for PointPredictive
Let Vector One IT Solutions help you design and implement a password managed solution for your company. Contact us today!
We are upstate New York’s premier IT managed service provider. We help our clients eliminate their technology frustrations and maximize the value of their investment in information technology. Our services include network & security assessments, cyber security policies, customized layered approach to security for defense in depth strategy, backup and disaster recovery, IT managed services, migration and implementation projects, network administration, help desk and support, product procurement, work from home solutions, and more. We can help you create and maintain a system that’s right for your organization with a focus on overall security, ease of use, and low total cost of ownership.

